Kill Chain Defense: A plain-English guide (and how to break it)
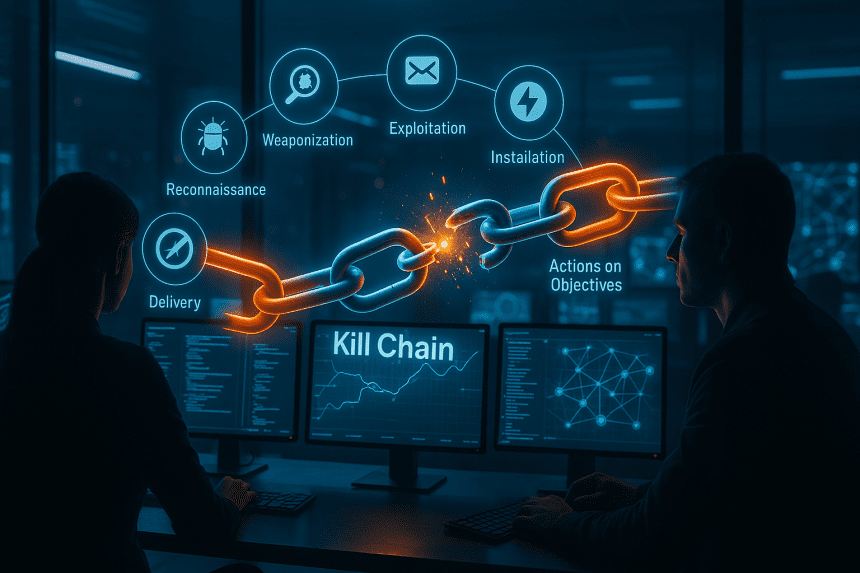
The Cyber Kill Chain is a practical way to visualize how intrusions unfold and where we can break them before damage occurs. First formalized by Lockheed Martin as part of its Intelligence Driven Defense® approach, it lays out the sequence an adversary must complete and gives defenders clear intervention points; Lockheed Martin’s own description highlights that the seven steps increase visibility and enrich analyst understanding of adversary TTPs. Put simply, it adapts the military “kill chain” concept to the digital battlefield a step by step method for identifying and stopping hostile activity sooner, as CrowdStrike’s primer explains.
At its core, the model is a lifecycle that helps tell a coherent story from first probe to final objective. Lockheed Martin popularized this narrative and tied it to intelligence driven courses of action so teams plan detections and countermeasures in advance, not mid crisis. The classic seven phases are widely documented reconnaissance (researching people, tech and exposed services), weaponization (pairing payloads with exploits), delivery (email, web downloads, supply chain and other channels), exploitation (triggering a flaw or a user mistake), installation (persistence to survive reboots and basic cleanup), command and control (remote direction back to attacker infrastructure), and actions on objectives (lateral movement, privilege escalation, theft, disruption or ransomware).These names and order match the original framework.
What makes the Kill Chain durable is the decisions those stages force. The framework encourages us to pre-position controls that shrink exposure early, detect and disrupt during initial execution, and starve and eject the threat if it reaches persistence or C2 exactly the “intelligence driven” mindset Lockheed Martin promotes. Modern teams blend this storyline with the MITRE ATT&CK® knowledge base: ATT&CK catalogs the “how” (concrete techniques) while the Kill Chain provides the “when” (campaign flow). CrowdStrike makes this complement explicit ATT&CK is a matrix of techniques, whereas the Kill Chain is the sequence of events so using both together improves detection design, hunting, and executive communication without losing technical precision.
MITRE’s own documentation underscores ATT&CK’s role as a globally accessible knowledge base of real-world tactics and techniques and shows how it spans enterprise platforms including SaaS, identity providers and IaaS.
Practically, we try to break the sequence as far “left” as possible. Before anything lands, reduce exposure with continuous asset discovery, timely patching, hardened email and web defenses, and SaaS posture checks tactics that deny easy wins in recon and weaponization, consistent with Lockheed Martin’s guidance and kill-chain-aligned white papers. At delivery and exploitation, hardened mail pipelines, sandboxing, browser isolation, and endpoint prevention either detonate malicious content safely or block it outright, buying time to quarantine hosts before persistence is installed; this emphasis on catching intrusions around stages three and four aligns with CrowdStrike’s educational content and services. If installation and C2 do occur, application control, MFA for administrative actions, and tight egress monitoring can sever lifelines and force re-compromise rather than letting a foothold become a breach, which maps to the mid-chain choke points in the original framework. Lockheed Martin Even late in the sequence, containment, token revocation, segmentation and data-loss controls can block exfiltration or encryption and protect crown jewels. CrowdStrike underscores correlating endpoint, identity and workload telemetry to spot multi-stage campaigns earlier and respond faster. CrowdStrike
Training should mirror reality. CrowdStrike’s red team/blue team exercises explicitly follow the cyber kill chain steps so organizations validate not only that alerts fire but that people make the right decisions and handoffs under pressure a rehearsal that builds the muscle memory needed when a real adversary sprints through the phases. CrowdStrike For executive communication, the Kill Chain provides a narrative that resonates: report which phases you reliably disrupt, where you’re blind, and how proposed investments shift detection and response earlier exactly the sequence-aware planning encouraged by Lockheed Martin’s intelligence-driven materials. Lockheed Martin
A few misconceptions are common. Reaching command-and-control does not mean the defender has already lost; late-stage detections and guardrails can still prevent data loss or encryption if they trigger in time, which is consistent with the framework’s intent to provide multiple intervention points. Lockheed Martin The model is not obsolete in cloud and SaaS environments; the same sequence applies even though signals and controls increasingly center on identities, tokens, APIs and control planes an evolution reflected in ATT&CK’s Enterprise matrix coverage of SaaS and identity providers. MITRE ATT&CK And MITRE ATT&CK has not replaced the Kill Chain; the two are explicitly complementary, with ATT&CK supplying granular technique coverage and the Kill Chain supplying campaign structure. CrowdStrike
Finally, both Lockheed Martin and CrowdStrike point toward a future where automation and AI accelerate offense and defense alike. While the claim that AI compresses timelines is still emerging evidence rather than settled fact, pairing human judgment with machine speed is the prudent path as teams test and measure real-world impact. CrowdStrike